

In today’s world, where a new data breach seems to pop up every day, cybersecurity is as critical as it is challenging. During our dinner discussion with 15 Bay Area CISOs, we asked what some of the biggest pain points were in cybersecurity today, as well as how the role of the CISO is evolving. Three issues that came up repeatedly were the infinitely large attack surface and ever-growing vulnerabilities; the need for security speed as companies bring products and services to market faster than ever; and resolving the discrepancy between a CISO’s view of security and a consumer’s view of security, particularly in the age of new data privacy regulations.
Addressing known vulnerabilities is a challenge in and of itself, but it’s the unknown vulnerability vectors that can generate the most concern for CISOs – we don’t know what we don’t know, and what we don’t know has serious potential for damage. Visibility into the attack surface only goes so far with human analysis; at this stage in cybersecurity, analyzing and improving security posture is no longer a human-scale problem. It is physically impossible to comb through all of the attack vectors, and traditional methods such as vulnerability assessment and penetration testing are able to look at less than 5% of the attack surface. A poor understanding of the attack surface leads to inefficiencies, frustration, vulnerability and ultimately breaches.
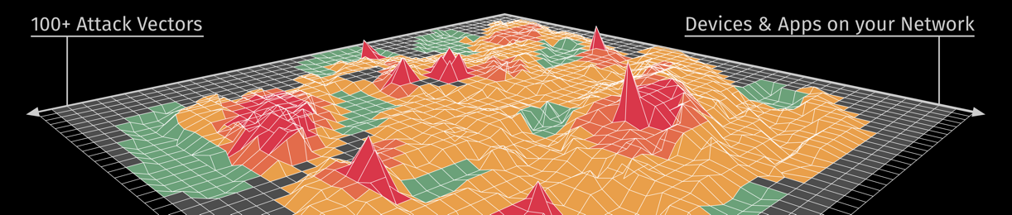
A new system that can assess all potential vulnerabilities and identify the most susceptible vectors is needed, but again, that system has to process and analyze massive amounts of information as cybersecurity is no longer a human-scale problem. AI can augment a company’s cybersecurity posture by providing significantly more visibility into the attack vector surface and thereby diminishing the magnitude of what we don’t know.
A second concern that emerged from our roundtable was the tension between decreasing production time and increasing cybersecurity needs. Today’s hyper-competitive environment means that companies are taking products and services to market faster than ever before. Concerns about security get left behind as product teams race to bring their offering to the market. This puts CISOs and other cybersecurity professionals in a challenging position, as they need to ensure security without hindering the business, and many of the security tools they currently use are slow and often ineffective.
The rise of microservices and open-source platforms further exacerbates this problem because they trigger false positives during vulnerability assessments. For example, current technology cannot accurately assess whether or not an identified vulnerability within an open-source library actually applies to a client’s use case.
Cybersecurity needs to be more agile to keep up with the pace of product development. One way to address this is to mitigate the number of false positives that plague IT ops. Between that and prioritizing vulnerabilities, it’s possible to secure an application quickly enough to release code multiple times per day.

A new system that can assess all potential vulnerabilities and identify the most susceptible vectors is needed, but again, that system has to process and analyze massive amounts of information as cybersecurity is no longer a human-scale problem. AI can augment a company’s cybersecurity posture by providing significantly more visibility into the attack vector surface and thereby diminishing the magnitude of what we don’t know.
Public breaches have led governments to impose new regulations related to data sharing and privacy, from GDPR to the California Data Privacy Law. These regulations make privacy professionals’ jobs more complicated as it shifts the responsibility of privacy further onto businesses. The new security posture has to account for these shifts in regulation and broader thinking.
At the same time, many CISOs around the table argued these regulations are nowhere near industry standard and fall short of their regulatory goals when it comes to security. This gap is made more difficult by consumer behavior – consumers will almost always choose convenience over security. Any cybersecurity solution must protect data privacy and be more convenient than the alternative.
One thing that the problems discussed all have in common is their outward-facing nature. Company data is no longer contained within the four walls of the office, or even within a limited range of hardware. Rather, it is constantly informed by and responds to external groups, whether it be at the level of architecture or end-user. This reflects a larger cultural shift in the way companies conceptualize information – and as this shift occurs, the role of the CISO evolves to become more strategic and cybersecurity continues to grow more crucial to a company’s success.
